You work hard to make your site awesome. And with all that work you put in, the last thing you want to do is lose your site to some malicious hacker. When it comes to hackers and WordPress, plugin vulnerabilities are one of the easiest ways for the bad guys to get in.
Because of its popularity, WordPress is a magnet for hackers. According to Sucuri’s Q1 2016 Website Hacked Trend Report, 78% of the hacked websites they deal with were running WordPress. And based on a survey from WordFence, 55.9% of WordPress hacks with known entry points were a result of plugin vulnerabilities. This makes plugins by far the biggest known contributor to hacked WordPress sites.
In this post, I’ll take a good hard look at some proactive steps you can take to prevent your site from becoming vulnerable to plugin exploits.
Why Do Hackers Want Access to Your WordPress Site?
If you’ve never been hacked, you may wonder what it is that makes hackers so interested in your WordPress site. For me, it was so that they could redirect my visitors to sketchy pharmaceutical sites. But that’s not the only reason they might want in.
But before I get to those other reasons, let’s start with something to make you feel a little better. It’s probably not personal. Most hackers are simply trolling for known vulnerabilities. These are typically crimes of opportunity, not passion.
Once they find a vulnerable target, they pounce in a few ways:
- Injecting links to artificially boost their sites’ SEO.
- Redirecting your visitors to different sites. The nasty redirects don’t affect you – so you might never know until you see your stats disappear.
- Installing malware on your visitors’ computers.
- Stealing your server resources for spam emails, DDoS attacks, or other nefarious purposes.
You don’t have to be a victim, though. Shoring up plugins as a vulnerability vector, as well as implementing other basic WordPress security tips, can protect you from most of these attacks. And you can keep your site humming along smoothly.
How to Mitigate Security Issues With Plugins
While it’s always possible for something to slip through the cracks, following these plugin security best practices will go a long way toward keeping your WordPress site safe.
Use a Quality Security Plugin
We’ve written plenty about WordPress security plugins, so I won’t belabor this point too much. But using a reputable security plugin can protect your site if a vulnerable plugin manages to slip through the cracks.
Don’t use it as your only line of defense. But as a last line of defense. It’s an absolute must.
Check If A Plugin Has Known Vulnerabilities
If you’re installing something popular like Akismet, you can safely skip this step. But if you’re installing a plugin with only a few thousand active installs, you should check for any known vulnerabilities before letting it run wild on your server.
To search for known vulnerabilities, you can use a website called WPScan Vulnerability Database. It’s run by WPScan and sponsored by Sucuri, who knows a thing or two about WordPress security.
You can either filter the plugins alphabetically or search for the plugin by name:
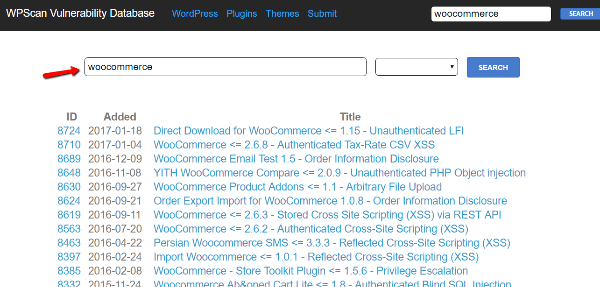
The site will give you both the exploit and date it was discovered. It will also give the version number for the vulnerable release. If the plugin has since released patches, you may no longer need to worry about the vulnerability.
Make Sure You Keep Your Plugins Updated…
WordPress has made it exceedingly simple to update plugins. Despite that, far too many people leave their core, plugins, and themes out-of-date. In Sucuri’s analysis, 56% of the hacked WordPress sites they looked at were running out-of-date software.
Also in their analysis, they found that just three out-of-date plugins accounted for a massive 25% of all the compromised WordPress sites they looked at. If you’re wondering, at the time of their analysis, those plugins were Gravity Forms, RevSlider, and TimThumb.
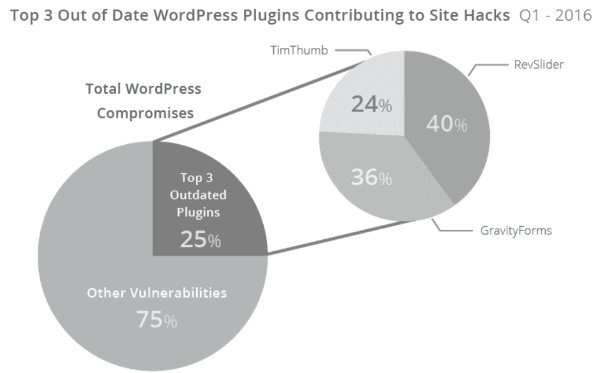
Image by Sucuri Hacked Website Report
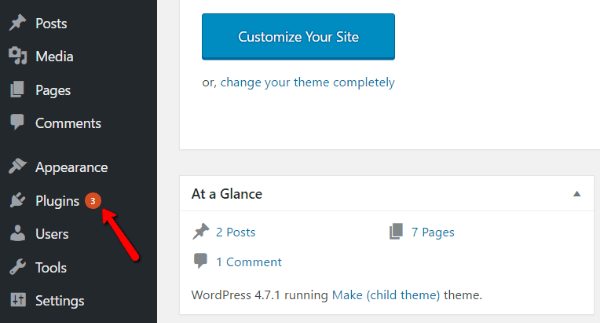
Don’t be that person whose WordPress site gets hacked because of out-of-date plugins. Literally, all you need to do is look for the red update notification and click a button!
…And Make Sure Developers Do, Too
It takes two to tango, though! If a plugin’s developers aren’t keeping it up-to-date, you can’t keep it up-to-date either. So when deciding which plugins to use on your site, try to look for those that receive regular updates from developers.
For example, on the WordPress.org directory, you can quickly tell the last time a plugin was updated:
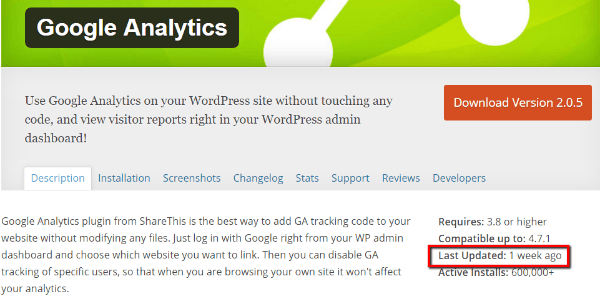
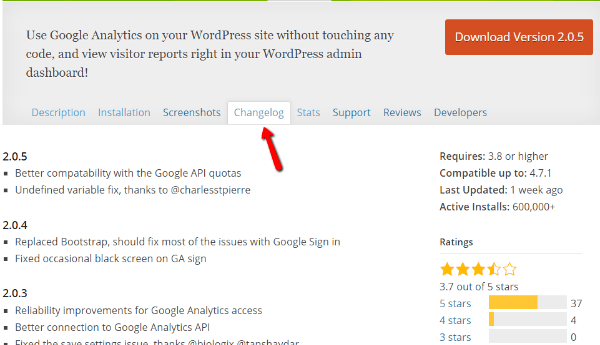
But that’s not the only thing you should look at. If you go to the Changelog tab, you can view the full update history (though not with exact dates). If developers are consistently pushing out updates to fix bugs, there’s a much better chance they’ll be around to patch any potential exploits:
Stay on Top of New Vulnerabilities
I’m sure you’re a busy person, so I’m not trying to add too much to your plate. But spending a little time every couple of weeks catching up on the latest plugin vulnerability finds can help you ensure you’re not running an exploitable plugin.
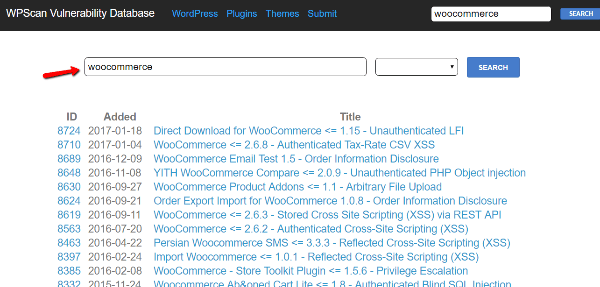
It’s not even a time-consuming thing – the website I mentioned earlier, WPScan Vulnerability Database, also lists out all of the recently discovered vulnerabilities:
Just pop in once or twice a month and give it a quick lookover.
WP Tavern also typically posts about new vulnerabilities in popular WordPress plugins, which makes it another good resource for staying up to date.
Be Wary Of Third-Party Plugins Not Listed in Directories
Being listed in the WordPress.org plugin directory or another major directory like Code Canyon is by no means a guarantee that a plugin is secure. But it is at least a mark that the plugin has passed some basic checks.
For example, humans review every plugin that’s submitted to WordPress.org. The vast majority are rejected initially, according to Pippin Williamson in 2014.
And while it’s always possible a vulnerability slips through, this review process gives you a much better chance at finding a secure plugin.
That said, reputable third-party plugins exist. If a plugin comes from a well-reputed developer (like Elegant Themes!), I don’t mean to push you away from using it. Be extra wary of plugins from unknown developers that aren’t listed in popular directories.
What To Do If You’re Using a Plugin With a Vulnerability
If the unfortunate situation occurs where you find yourself using a plugin with a known vulnerability, here’s what to do:
First, check for updates. Developers will quickly push out a fix if it’s a well-supported plugin. Update the vulnerable plugin as soon as the fix comes out. Not a minute later.
Second, if there are no updates and the developer doesn’t seem to be responsive to the issue, disable the plugin. I know it’s not easy to disable a plugin that you rely on, but when the alternative is opening up your site to exploits, you really have no choice.
Sometimes you might be able to use a WordPress account with lower permissions to skate by (e.g. Author or Editor). For example, if the vulnerability requires an admin session, like a recent W3 Total Cache vulnerability, using an account with lower privileges can bypass the issue. But this approach will not fix all vulnerabilities – so buyer beware.
Wrapping Up
Every website admin’s worst nightmare is getting hacked. But with the help of these proactive plugin security measures, combined with regular backups and good general security practices, you can harden your site and lower your chances of being exploited.
Just remember to:
- Stay updated
- Check for known vulnerabilities
- Not install shady plugins
Site ever hacked due to an exploitable plugin? What steps did you take to remedy the situation?
Article thumbnail image by PROSTOR / shutterstock.com




Great article Brenda. WordPress being so user friendly opens a lot of vulnerability to unsuspecting victims.
How about when a theme or plugin has a major update that breaks your site? I hate to say it, but sometimes that’s a headache that’s not worth dealing with.
Depends if the theme of plugin update addresses a security issue.
Awesome articles. I am using iThemes Security and never faced any problem from a long time. I am also using third party security scanner such as sucuri to scan my site regularly. Thank You
Although disabling a vulnerable plugin can be effective, there’s still a big difference between “disabling” a plugin and “deleting” a plugin.
It does depend on the kind of attack, but I believe it’s good to also mention the implication of that difference:
When a plugin is disabled, the files can still be accessed by an attacker, either directly or indirectly.
When a plugin is deleted, the files should no longer be present. Of which you’ve then eliminated at least the most prominent and destructive effect of an attack; i.e. file and SQL injection.
plz guide me which all plugins do i use to avoid wordpress vulnerabilities completely
Gravity Forms is such a popular plugin. Are you suggesting that this is bad to use?
Gravity Forms is fine to use. Also it has an automatic update option in the settings, so if there are any security updates for GF core, then you do not have to worry about those.
Is disabling a plugin enough though? Can’t it still be exploited through the db? I would imagine the best way would be to just remove it all together – thoughts on this?
Dear Brenda,
Thanks for the tips!
Maybe these two things help a lot:
1. Update Core and plug-ins autmatically by putting Some Simple code in your config-file. You will allways be up-to-date
2. Install the free plug-in Wordfence to check for hacks and prevent them.
That helps for me.
What do you think of that Brenda?
Greetings,
Chantal from Holland
I’d be a little bit cautious with just setting everything to auto-update as this could have drastic effects on the site in question. For example, a core update may break custom code in a child theme, or more fundamentally break a theme that doesn’t support the new version of core yet – this has happened to themes I’ve bought through various theme markets as it’s taken a while for them to be updated and released.
Another good example is the recent update to WP-Spamfield. This took out websites completely! Lots of people reported it leaving their sites dead and after trying it on one of my sites and having to revert back to the previous version, I’m loathed to let anything auto-update without having control over it.
There’s no simple solution to this other than being diligent and updating as soon as you can once you’re happy it won’t break the site.
Just my tuppence-worth.
+1
What about restoring sites that were hacked?
All in all, WP + common sense should be a great solution like any other web platform. I’d be surprised if a standalone, proprietary website will be much safer then using WordPress.
Of course, some hacks and vulnerabilities will be discovered here and there, but you could probably fix this easily We all remember Revolution Slider 🙂
What about searching themes for vulnerabilities too? What’s site is good to check on themes (like the plugins)?
WP Theme Check
https://wordpress.org/plugins/theme-check/
In the same website you can do both (themes & plugins)
Awesome article. I know I had my shares of hacked sites and of course you said it. I failed to update my plugins.
Thank you Brenda Barron for this post. it serve as the perfect reminder for anyone who actually care about their site or clients.
Great post . How about forums communities, letting customers to login , register any advice how to protect yourself ?